As 2024 begins, it’s time to look at IT security trends, which will make or break brands this year. IT security teams and enterprises in 2024 should prepare their response plans to mitigate cyber risks.
In 2023, enterprises took brave steps by investing in new security technologies, installing new tools, or updating their cyber stacks. Still, they might see riskier cyber-attacks.
However, they should continue to update, adapt, and align security solutions according to business needs. The solutions should keep critical data and overall IT security posture secure and intact.
Secureworks and Cybersecurity Ventures’s report Boardroom Cybersecurity Report on Cybercrime,
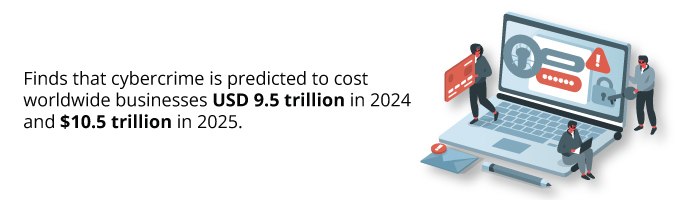
These costs are determined based on losses such as:
- Theft of intellectual property
- Personal and financial data breach
- Post-attack disruption to the ordinary course of business
- Restoration and deletion of hacked data and systems
This makes security and risk management leaders refine their investments across technology and skills to implement their cybersecurity programs.
Gartner’s Risk Management Trends 2024 report finds

Leaders need to implement a security strategy for the evolving digital age, where security skills need to be cutting edge.
So, here are the top three IT security trends to look out for in 2024!
Large-scale Social Engineering Attacks
The use of Generative AI is rising, both positively and negatively. As companies use it to simplify their multiple business processes, threat actors used it to launch multiple attacks.
Attackers will use it in their social engineering campaigns using LLMs to mimic high-level decision-makers and executives to drive operations- email phishing.
By this, it will be easy for them to take all data and manipulate systems like ChatGPT, chatbots, and other digital channels to manipulate clients and customers. The attackers are using various methods- email phishing, ransomware, and data theft to name a few.
This social engineering attack trend will be riskier and more hazardous for companies dealing with huge amounts of data.
Solutions like email spam filters will be insufficient to combat this. The ways to combat these attacks are:
- Implementing multi-factor authentication using OTP codes
- Use cloud-based WAF to monitor web apps, websites, malware installations
- Employ an identity management system for email ID verifications, social profiles, and companies
- Obtain SSL certificates to encrypt data, emails, and communication channels to stop interception of communication
Insider Threats
Insider threats are prevalent but often overlooked in organizations. They develop among employees or business partners who intentionally or accidentally misuse their access.
Threat actors target employees and recruit them as insiders by promising them money in exchange. They do it in exchange for providing access to systems that keep sensitive data and company credentials.
This is becoming a popular strategy and is growing only. According to IBM’s Cost of a Data Breach Report 2023 report, data breaches due to malicious insiders costed USD 4.90 million on average in 2022. In 2021, it costed USD 4.45 million, which increased by 9.5% in 2022. Insider threat actors and incidents have exposed 1 billion business records during this period.
2023 Insider Threat Report by Cybersecurity Insiders reveals:
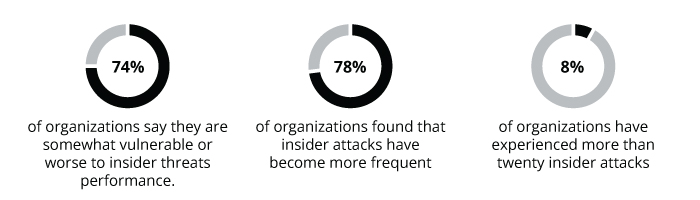
Considering these insights, companies should adopt advanced tools, technologies, and processes for detecting insider threats.
They should look into gaps while any data is being shared. One important way is to look into the context of existing data and understand their exposure.
Based on this, auto-labeling of data should be done, which can discover unauthorized and sensitive data through categorizing.
Additionally, it’s also important to ensure that escalation protocols are simple to use and include steps for employees if they are asked to share their credentials from the enterprise network.
Protocols will play an equally crucial part for companies in 2024 as adopting advanced tools, technologies, and processes for detecting insider threats.
Misconfiguration-based Threats
As companies continue to shift their applications and systems to the cloud, no matter how strong their security systems are during configurations, they might still have vulnerabilities.
As a result, secure integration and cloud networking systems with internal and endpoint security are necessary.
The continuous adoption of the cloud, the ongoing hybrid workforce, and the evolving regulatory environment are forcing security and risk management (SRM) leaders to improve their security and risk management spending.
A report Gartner Forecasts Global Security and Risk Management Spending to Grow 14% in 2024 predicts that the continuous growth in public cloud services will boost companies to spend on cloud security tools.

Furthermore, companies should focus on the fact that their cloud service providers should have rigorous security-based architecture.
Also Read: The Evolving Landscape of IT Security Threats: What Businesses Need to Know
Conclusion
While cyber risks are increasing and changing the business environment, it is more critical today for organizations to build and optimize a robust cybersecurity program.
By taking cybersecurity initiatives for these expected risks in 2024 will help security leaders to:
- Secure new environments
- Protect against expanding attack surface
- Adapt security capabilities in new ways
- Install better security solutions through automation
For more such updates follow us on Google News ITsecuritywire News. Please subscribe to our Newsletter for more updates.









