With ongoing rapid technological advancement, security threats have evolved beyond the digital realm, encroaching on physical infrastructures and the core of organizational operations that can jeopardize safety, economics, and system reliability. As the scope of threats expands, the challenge lies in seamlessly blending traditional and modern protection measures. To help organizations address the pressing need to unify physical and information security mechanisms, global research and advisory firm Info-Tech Research Group has published its latest blueprint, Integrate Physical Security and Information Security.
“The convergence of operational technology (OT), the Internet of Things (IoT), and Industrial IoT (IIoT) is transforming the security landscape,” says Carlos Rivera, principal advisory director at Info-Tech Research Group. “This convergence is being driven by the adoption of sophisticated access control systems such as electronic locks and biometrics, as well as the digital transformation of security through cloud technologies. As organizations face increasing security risks, they are unifying their physical, cyber, and information security systems to gain the long-term benefits of a consolidated security strategy.”
According to Info-Tech’s research, physical security systems integration can be complex due to a blend of proprietary devices, protocols, and the coexistence of analog and digital technologies. While there’s a clear need for open architecture and detailed planning, territorial protection by existing IT and physical security managers may limit security visibility and hinder security integration. Additionally, integration poses challenges in staffing, training and awareness programs, and the dependency on third-party technologies and their migration plans.
Also Read: Robust Multi-Protocol Label Switching (MPLS) Security Practices
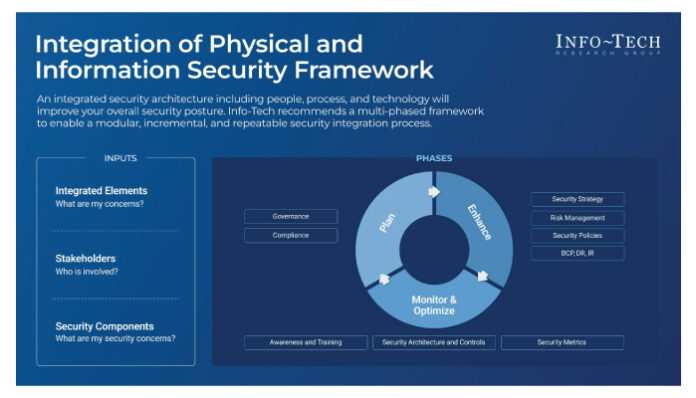
The new resource highlights Info-Tech’s recommended approach, which is a modular, incremental, and repeatable process to integrate physical and information security, enabling organizations to:
- Plan and Engage Stakeholders: Assemble the right team to ensure the successful implementation of the integrated security system. It’s essential to decide on the governance model and clearly define the roles and responsibilities.
- Enhance Strategy and Risk Management: Develop a physical security system that is interoperable with most technologies. The design should be flexible, require minimal customization, and remain functional and integrated, even with challenges like proprietary configurations, complex customization, and siloed operations.
- Monitor and Optimize: Identify the best strategic, realistic, and risk-based architectural design. Next, perform an evaluation of the security systems and program by understanding what, where, when, and how to measure and report the relevant metrics.
Physical security is also often part of facilities management. As a result, there are interdependencies with both internal departments, such as IT, information security, and facilities, and external parties, like third-party vendors. Info-Tech advises that IT leaders, security leaders, and operational leaders should keep the big picture in mind when designing and implementing the integration of physical and information security.
For more such updates follow us on Google News ITsecuritywire News. Please subscribe to our Newsletter for more updates.