Phishing scams are one of the common forms of cybercrime, and they continue to grow in popularity. Failure to recognize them and not taking timely measures to tackle them can affect businesses negatively.
The internet has revolutionized our lives and work, connecting us with people and information worldwide. However, with this convenience comes the risk of very damaging cybercrime. One of the most common and dangerous forms of cybercrime is phishing.
In a phishing scam, cybercriminals impersonate a trusted entity, such as a bank or retailer, to trick users into revealing their sensitive information.
Phishing scams are becoming increasingly more sophisticated, making it more challenging to identify fraudulent emails or text messages. if unidentified, a phishing scam can result in financial loss, identity theft, and other serious consequences
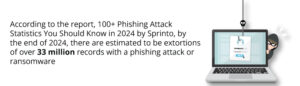
This article discusses the different types of phishing scams, how to recognize them, and, most importantly, how to protect businesses from falling victim to them.
Common Phishing Scams
Phishing scams can take many different forms, but there are some common types that you should be aware of.
-
Email Scams
Email scams are the most common form of phishing. These scams often look like they come from a legitimate source, such as a bank or an online retailer.
According to the same report by Sprinto, 1.2% of all emails sent are reported malicious in 2024, which is 3.4 billion phishing emails per day. This means that 1 in 4,200 emails sent is a phishing scam.
The email will typically ask to click on a link or download an attachment, taking you to a fake website designed to look like the real one. Criminals can access your account once you enter your login credentials or other personal information.
-
Smishing Scams
Smishing scams are similar to email scams but use text messages instead. You’ll receive a text message that looks like it’s coming from a legal source, such as your bank or a shipping company. The message will typically ask to click on a link or call a phone number to resolve an issue with your account.
Once you do, you’ll be asked to enter your personal information, which the criminals will use to steal your identity.
Also Read: Seven Alarming Signs of Spear Phishing Attacks and How to Prevent Them
-
Spear Phishing Scams
Spear phishing scams are more targeted than other types of phishing.
According to the report 81 Phishing Attack Statistics 2024: The Ultimate Insight by Astra, 65% of attackers have opted for spear phishing as their prime method of attack.
In these scams, criminals research their victims to create a more believable email or text message. For example, they might use your name or job title in the message to make it look more legitimate. These scams can be harder to spot because they’re so personalized.
- Clone Phishing Scams
Clone phishing scams are emails where the criminal creates a copy of a legitimate email. They’ll modify the email slightly to include a link or attachment with malware or a fake login page. The email will look like it’s coming from a legitimate source, but the link will take you to a website designed to steal data.
How to Avoid Phishing Scams
Here are some tips to help you avoid phishing scams and protect your personal information:
-
Beware of unsolicited emails or messages:
If you get an email or message from an unknown email address or sender that looks suspicious, do not click on links or download attachments.These emails may have malware that can steal the business data and compromise your device.
-
Verify the sender’s legitimacy:
Verify the sender’s legitimacy before clicking on links or giving out your personal information.Cross-check the phone number or the email address to ensure it is from a legitimate source. If in doubt, contact the firm directly using their official website or phone number to ensure the email or message is genuine.
-
Look for spelling and grammar errors:
Phishing emails often contain spelling and grammar errors. Legitimate emails from reputable companies are usually professionally written and error-free.
-
Avoid clicking on suspicious links:
Phishing scams contain links that lead to fake websites that look real.These websites are designed to steal your personal information. Before clicking on links, hover over them to see the URL. If it looks suspicious, you should not click on it.
-
Use anti-phishing software:
Anti-phishing software can detect and block suspicious emails and links. This can be your first layer of security. You can install anti-phishing software on your device or use it as a browser extension.
-
Keep your software up-to-date:
Keeping your software up-to-date is essential. Cybercriminals often exploit vulnerabilities in outdated software to steal personal information or infect devices with malware.
-
Use strong passwords:
Strong passwords protect personal information. Use a combination of lower and upper case letters, numbers, and special characters for a strong password. Avoid using the same password for your different accounts.
-
Enable two-factor authentication:
Two-factor authentication delivers an extra layer of protection to accounts. It requires a second layer of authentication, before accessing any account.
Summing Up
Cybercriminals continue to create new and sophisticated methods to trick people into revealing their personal and sensitive information.
However, by staying aware of the different types of phishing scams and following the tips to avoid them, you can protect yourself and your business from becoming victims.
It’s essential to exercise caution when opening or responding to unsolicited emails or messages. Verifying the sender’s legitimacy is necessary by checking on the source. Always check your email address or phone number and look for spelling or grammar errors. Avoid clicking on suspicious links, and use anti-phishing software to protect your devices.
Moreover, keeping your software up-to-date is crucial. Cybercriminals often exploit vulnerabilities in outdated software to steal business data or infect devices with malware.
Following these best practices can reduce the risk of falling prey to phishing scams and safeguard your sensitive information.
Check Out The New ITsecuritywire Podcast. For more such updates follow us on Google News ITsecuritywire News.









