Digital transformation has made infinite third-party connections for every application and enterprise software. With increasing integrations, risks rise. It has never been more crucial to secure third-party risk management effectively.
According to SecurityScorecard close encounters third-party report,
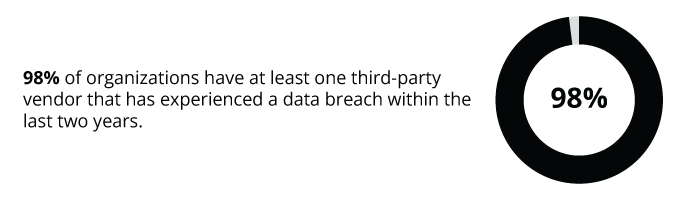
Why organizations need third-party risk management
When a third-party vendor gains access to an organization’s network, potential vulnerabilities become a shared problem. Even a single risk factor or compromise can have serious consequences for both.
It may result in a whole range of unwarranted situations. Some of them could be:
- Customer Service Disruption
- Reputational damage
- Supply Chain Disruption
- Financial Fraud or Exposure
Above all, there is a very real risk of Violation of regulations or compliance, which could mean the cost of all of the risks above.
Enterprises must be extremely conscious of risks when integrating third-party vendors to their solutions or infrastructure.
Many cyber security programs, however, take a one-size-fits-all approach to third-party risk assessment. This results in an ineffective process that frequently leads to risk acceptance rather than risk mitigation.
Third-party risk management provides numerous benefits for businesses. It helps organizations avoid business disruptions by monitoring third-party vendor security. It can also provide early warning signals of potential security risks through these connections. These signs could often be the only way for enterprises to take immediate action, and manage these third-party risks well.
One of the bigger outcomes of a vulnerability through third-party associations is the loss of reputation or data breaches. An early warning may protect brand reputation by monitoring potential incidents and reducing risk exposure in third-party integrations.
These factors are important in increasing customer trust, lowering costs, and reducing operational risk.
Also read: Lead Cybersecurity Risk Management in Three Crucial Steps
Strategies for Third-Party Risk Management
-
Develop A Third-Party Risk Management Program
A critical step in successfully managing third-party risks is to develop a programmatic approach to the task. This will include a governance structure that establishes duplicable processes and standards. These can be applied in integrations with multiple third parties.
An effective TPRM program should align with regulatory and data protection requirements and the organization’s risk tolerance.
A useful strategy here is to use a rubric to understand and categorize third parties based on the risks they pose. A rubric, for example, could be used to grade third parties as low, medium, or high. A rubric also enables organizations to quickly identify the level of assessments and mitigating controls required for each third party, with those labeled high receiving the most scrutiny and mitigations.
Experts say third-party risk management frameworks and software can help technology leaders establish programmatic approaches to TPRM. However beneficial as those moves may be, studies show that many organizations have yet to make such changes.
According to Panorays’ 2024 CISO Survey,

-
Identify The Risk That Matters
The three most pressing risks are cyber security and data privacy. These two have the highest impact on the company. The costs of the consequences and liability associated with breaches will increase as ransomware attacks become more frequent. Third-party associations lay bare that inlet for high-security vulnerabilities.
The main challenge here is that enterprise security leaders are not responsible for all of these risk domains. They need to depend on and engage with the security leadership of relevant stakeholders. The risk also impacts the business teams.
This also means that business risk owners must be identified for each risk domain so that responsibility does not fall solely on security teams.
According to a Gartner survey conducted in 2023, organizations can improve their effectiveness by 18% just by collaborating closely with other third-party risk functions. This way, they can redirect responsibility for non-cybersecurity third-party concerns.
-
Create an Up-To-Date Inventory of Third Parties
CISOs cannot effectively manage third-party security threats unless they have a complete picture of the third parties in their organization.
This is an especially difficult task because business units now deploy increasing technology. Today, every business function is enabled by IT, and in most companies, each function has a security shield for its solutions. This has largely replaced a centralized IT function dedicated to inventorying all technical assets.
As a result, CISOs must implement strategies for identifying and maintaining an accurate, comprehensive, and current inventory of third-party security risks.
Software solutions can help in this situation, but there need to be more steps to help identify problems with third parties. Most of these will go beyond tools and work more on teams, risk awareness, and security policies at the vendors’ end.
-
Determine Risk Controls
Effective risk management must focus on controls that reduce risk in the supply chain ecosystem. There will be different controls for different types of third parties CISOs need to manage them as per their unique risks.
For example, SaaS (software-as-a-service) vendors with access to corporate data will need different controls than an on-site services provider or hardware vendor.
Organizations themselves implement some of these controls, while others will be the responsibility of a third party.
According to Gartner’s third-party management research,

Once mutual contingency plans are in place, prioritize strengthening them for third-party engagements that pose the greatest cyber security risk. Create incident playbooks specific to third parties, conduct tabletop exercises, and define a clear offboarding strategy, including timely access revocation and data destruction.
-
Treat Third Parties Like Allies
Critical third parties should be considered allies, and the engagement strategy must shift from policing to partnering.
Building mutually beneficial relationships promotes greater transparency, allows third parties to implement controls more easily, and improves collaboration during a cybersecurity incident.
In a hyperconnected world, third-party supplier risk is the organization’s risk. It’s critical to help them mature to protect the enterprise better.
It is also critical to monitor internal information and, if necessary, implement additional controls to protect the organization’s environment in response to your findings.
-
Ensure The Executive Team Knows the Third-Party Risks
Third-party risks include more than just cybersecurity threats; they can cripple the business in its entirety. They can impact all aspects of the organization, including its operating ability.
However, many organizations fail to manage those risks comprehensively. Some companies shave a dedicated executive for this job – a Chief Risk Officer. That is actually a good strategy to ensure that third-party risks are taken as seriously as other cyber security risks.
In companies that take a siloed approach, the CISO handles cybersecurity-related third-party risks. Other executives take responsibility for those that may affect their respective functions. Such an approach can result in blind spots and gaps.
CISOs can and should take the lead in educating the board and executive team about the cascading and interconnected nature of third-party risks to the organization.
In other words, CISOs should showcase the impact of an attack on enterprise leaders. He or she should inform the Board that a third-party cyber incident could cause a security breach at their organization. This single wormhole could result in lost business, regulatory fines, and reputational damage.
The executive team must understand that successful risk management begins with the board and the C-suite.
Conclusion
Organizations should form a strong risk intelligence team to continuously monitor third-party vendors. They should also ensure leadership support when investing in due diligence and regulatory compliance.
They should also conduct regular audits to assess vendors’ compliance with security, health, and governance standards. There is a need to invest wisely in IT infrastructure and security to strengthen defenses against external threats.
For more such updates follow us on Google News ITsecuritywire News. Please subscribe to our Newsletter for more updates.









