A successful Distributed Denial of Service (DDoS) attack threatens the company’s infrastructure, reputation, and costs them millions. Hence, having a DDoS mitigation solution that protects them from various DDoS assaults is essential.
As per a recent report by Radware, “Multi-Cloud Application Protection Report 2023,”
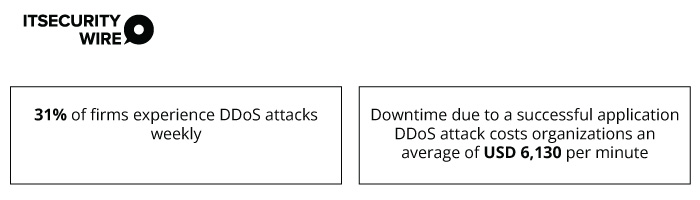
Here are two DDoS attacks firms must be prepared for in 2024.
1. Layer 7 (L7) Application Attacks
Layer 7 application attacks target the application layer by disabling specific functions of website/web app by overusing them.
Radware’s report also states-
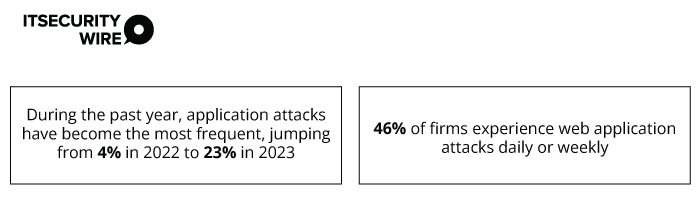
While these attacks are carried out using IoT devices, hackers use these attacks to distract businesses from ongoing security breaches. Though they are low-volume attacks, they can cause downtimes, affect business continuity, and strain web apps.
L7 attacks are hard to detect because they attack app-specific resources. They use malicious bots to make legitimate requests. The simplest L7 attacks, such as those targeting login pages with random user IDs and passwords, can still critically overload CPUs and databases.
Here’s how businesses can mitigate L7 application attacks.
-
Deploy Web Application Firewall (WAF)
A WAF helps manage, filter, and analyze traffic from various sources. It uses customized rules and policies to respond to attacks faster.
These firewalls assess the layer 7 traffic and feed data directly to businesses. This helps them identify malicious traffic disrupting the services.
-
Use Behavioral Analytics
Behavioral analytics uses AI and ML to observe and make notes of user and entity behaviors. They help detect abnormal activity or traffic that doesn’t match the usual patterns. It uses advanced analysis, data from logs and reports, and threat data to detect abnormalities that might indicate malicious behavior.
-
Captcha Verification and JavaScript Challenges
Captcha verification is a web approach that detects whether the user is real or a spam bot. Captchas challenge the users with manipulated letters or symbols which requires human ability to decode.
JavaScript challenges filter out requests from botnets or malicious computers. Legitimate browsers have a JavaScript stack to understand and pass the challenge. DDoS bots lack a JavaScript stack and struggle to respond to these complex challenges.
2. Ransom DDoS Attacks (RDoS)
Financially motivated hackers carry out RDoS attacks. They target online resources such as websites and web APIs to render online services inoperable. This extortion-based attack disrupts an organization’s online services, business, productivity, and reputation.
An RDoS attack starts with the attacker delivering a private message. They request payment of a certain ransom amount to prevent the organization from being attacked by a DDoS assault. In some cases, the ransom demand increases daily if the victim refuses to pay.
To make the ransom letter more credible, an attacker often mentions about a demonstration DDoS attack. It is an attack launched before the payment deadline. They do this to validate the legitimacy of the threat.
Here’s how firms must respond to such attacks.
-
Do Not Pay and Alert the Security Team
Paying RDoS attackers can be damaging and doesn’t guarantee they will leave the organization. Addressing or paying their demand potentially “identifies” the target as company willing to pay under threat.
Paying the ransom allows threat actors to improve their capabilities and motivates them to continue their campaigns.
Victims must alert their security provider to the threat regardless of the severity. Provide them with the ransom letter and have them jointly monitor further activities.
Informing the security provider can help them prepare, closely monitor the traffic, and assign tighter security mechanisms.
-
Monitor Possible Demonstration Attack
Ransom messages include the threat of a minor precursor attack that shows the attacker’s capabilities and threat’s viability.
A demonstration attack can be a small assault that requires assessing network logs for traffic spikes representing a small-scale DDoS attack. These logs can be checked by the network team, security team, ISP, or cloud security provider. Unfortunately, these attacks result in volumetric assaults that can take networks and websites offline.
Hence, firms must closely track such attacks to seek insights on the threat’s severity, attack vectors, and sources. This will help them prepare for any potential subsequent attacks.
The absence of a precursor attack does not mean an RDoS attack will not follow. Therefore, closely monitor the signs of a precursor attack to understand the gravity of the threat.
-
Educate the Employees
RDoS ransom notes are sent randomly to random employees within the target organization. Sometimes, these notes include instructions to pass this threat on to the relevant people.
Hence, firms must educate employees about RDoS attacks and the steps to take if a ransom note reaches them. Set up a point of contact to handle relevant threats passed on by the victims.
Communicating relevant information early and quickly can help the companies be aware of a ransom note.
Also Read: Strategies to minimize multi-vector DDoS attacks
Conclusion
As per a recent report by A10 Networks, “2022 DDoS Threat Intelligence Report“,
- Approximately 423,096 bot agents were tracked
- Bot activity typically changes with each reporting period. In H2 2021, an 8% decrease in the total number of bots was observed
The demand for solutions for business needs and 5G tech has accelerated the expansion of IoT globally, creating a massive pool of attack surface.
In 2024, the threat landscape continues to evolve, with hackers launching more sophisticated DDoS attacks aiming at new targets. These attacks are expected to continue as botnets and inexpensive DDoS-as-a-service platforms proliferate.
For more such updates follow us on Google News ITsecuritywire News. Please subscribe to our Newsletter for more updates.









