Firms mostly rely on open-source software (OSS), using third-party and open-source libraries and components. These apps boost the speed and lower development costs. However, firms find handling Open Source software security risks challenging.
If these open-source components contain exploitable vulnerabilities or malicious functionality, they can expose the firm’s applications to attack. Hence, OSS security is vital in managing the risks that open-source code poses to applications, data, and systems.
What are the Open Source Software Security Risks?
1. Gaps in Public Domain
Software’s source code, once put in the public domain, is publicly accessible. Cyber attackers can also access the code to look for security gaps.
One of the biggest Open Source Software Security Risks is its openness. Once any developer identifies a vulnerability, it can quickly become public knowledge across the free open-source community. If it is made public, there are high chances of exploitation, even before a fix is found!
2. Unmaintained and Malicious Packages
Developers may likely abandon packages that a firm’s systems rely on. This may lead to difficulties in patching future vulnerabilities. There is also a possibility that the code may lack necessary security mechanisms like updated cryptography.
Hackers target software supply chain security by exploiting companies’ reliance on open-source code.
Attackers can trick developers into introducing vulnerabilities or malicious functionality into their apps. They can build malicious lookalike libraries or infect trusted ones with malicious code.
3. Unpatched Vulnerabilities
“Regardless of whether it is open source or proprietary software, unpatched and out-of-date systems can be a source of compliance issues and security vulnerabilities.”
“In fact, most vulnerabilities exploited are ones already known by security and IT teams when a breach occurs.”, says Jenkins.
Volunteers often maintain OSS rather than a company’s dedicated development team. This slows the process of identifying and patching vulnerabilities in the code. Apps using these vulnerable components may be open to exploitation.
4. No Warranty
OSS has no warranties regarding its security, support, or content. Volunteers do support many projects, but their development contracts are not permanent.
Moreover, they evaluate the software for security issues and provide support via open forums. If not under contract, they may not provide accurate guidance. If they don’t, no company can take action against them due to lack of commitment.
Verifying whether the code is original and not taken from a third-party source with established copyrights becomes difficult. This means that firms are responsible for infringement if they use open-source software containing a code with infringed rights.
5. Loose Integrations Oversight
Firms often have insufficient or non-existent review processes when using particular open-source components. Different teams or developers might use multiple versions of the same component. They also might be unaware of conflicting functionality or licensing.
These issues can occur due to inadequate software security, functionality, and communication knowledge. There may be a shortfall in tracking and documentation protocols as well.
Open-source components do not have built-in controls to prevent the use of multiple or incompatible versions. They typically rely on the user to verify proper use.
6. Operational Shortages
When using open-source, it is essential to keep track of the components used, their version, and how they might interact with other components.
At the same time, it is critical to license and monitor updates and patches, including their impact on functionality.
Components with unnecessary functionality can add complexity to your system without delivering any benefit.
7. Flawed Developer Practices
There is an increased risk when the code is copy-pasted from open-source software instead of integrating the whole component. The code cannot be tracked for licensing or security purposes if it is a copy-paste job.
Also, developers might not transfer components using a binary repository manager or shared network location for collaboration. They might do it by email. This leaves the code vulnerable during transfer, allowing malicious functionalities to enter.
What are the Strategies to Mitigate OSS Security Risks?
1. Use Automation
Detecting and addressing vulnerabilities in OSS is a challenge. It is essential to detect gaps in open-source code in their environments and update the list regularly. Tracking unsecured software components and deploying patches to all security vulnerabilities is important.
“Applying automation can help streamline patching operations. It can help streamline daily operations as well as integrate security into processes, applications, and infrastructure from the start.”
 “Automated testing ensures that the codebase remains stable and functional, while automation tools can help manage dependencies by checking for updates and automatically integrating them into the project. An automation workflow for patching can speed operations, reduce the risk of errors, and improve consistency across systems.”, says Chris Jenkins, Principal Chief Architect, Cybersecurity Strategy and Adoption at Red Hat.
“Automated testing ensures that the codebase remains stable and functional, while automation tools can help manage dependencies by checking for updates and automatically integrating them into the project. An automation workflow for patching can speed operations, reduce the risk of errors, and improve consistency across systems.”, says Chris Jenkins, Principal Chief Architect, Cybersecurity Strategy and Adoption at Red Hat.
2. Inventory Management
As per a recent report by Synopsys, “Open Source Security and Risk Analysis Report,”
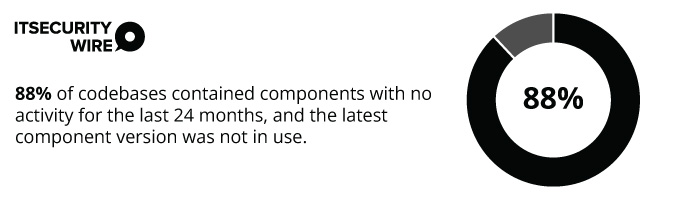
Integrating automation can help firms know the benefits of a full inventory of applications they have. This allows them to fight the cyberattacks caused by unidentified vulnerabilities in the source code.
“They need to take an inventory of the open source technologies currently used in their organization, and if any are not obtained from known, trusted sources, they need to understand the risks.”, agrees Jenkins.
3. Ensure the Used Components are in Compliance with Open-source License Terms
Firms must ensure that they use open-source components with a license to avoid legal risks. Identifying acceptable licenses for components used in software development is vital to prevent legal issues.
Synopsys’ report also stated that-
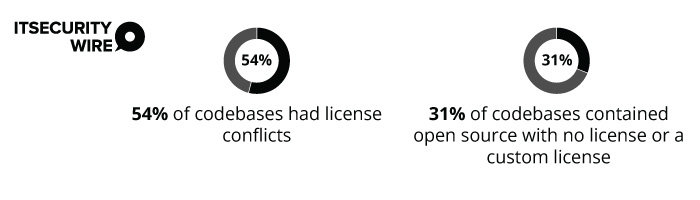
Consider how the component is linked, the deployment model, and the intended distribution scheme. After identifying the acceptable licenses, firms can comply with the requirements stated in those open-source licenses.
4. Employee Training
It is a challenge to hire professional experts in both development and security. Hence, effectively training the teams so that they can approach the issues from both ends is crucial.
“Not everyone in the organization needs to be a security expert, but everyone needs to be aware of the security issues within their specific area. For developers, it is often enough to understand that an issue has occurred and can be remediated by taking action to replace a component or upgrade a component.”
“A wider issue that does require training is with regard to the context of a vulnerability. It requires expert knowledge of a vulnerability, the environment, and the technology stack to be able to identify whether a particular vulnerability is relevant based on the circumstances for an exploit.”, adds Jenkins.
Also Read: Four Best Practices for Safeguarding Open Source Software
Conclusion
As per a recent report by Red Hat, “The State of Enterprise Open Source,”
- 89% of IT leaders believe enterprise open source is as secure or more secure than proprietary software.
- 80% expect to increase their use of enterprise open-source software for emerging tech.
While many believe open-source is more secure than proprietary software, security risks still exist. They are as deadly as in proprietary software and need proper management. Firms must check for vulnerabilities before using any open-source code or software.
They must maintain an accurate inventory of all open-source code. There must also be a process of continuous scanning for vulnerabilities. If identified, there needs to be a prompt addressal. Investing in DevSecOps practices and employee training about secure coding helps reduce unintended security gaps.
Jenkins says,
“A good balance between security, regulation, and business considerations is crucial. But this is easier said than done: it requires a real culture shift within organizations. Open communication, collaboration, and personal interaction between teams are needed to foster trust and effective support so that security priorities can be better aligned with overall business objectives.”
“Education and training remain fundamental to achieving that culture shift. Training teams on best practices, emerging threats, and new technologies remain as important as ever. As organizations migrate to newer technologies and embrace cloud-native development, this knowledge is much needed to ensure a successful transition without compromising security.”
Firms can benefit from open-source components and software only if they best implement practices to manage the risks properly.
For more such updates follow us on Google News ITsecuritywire News. Please subscribe to our Newsletter for more updates.









